Shorten approval cycles for data enablement with policies directly connected to native data controls in your data & AI systems.
Data Use Governance
Deliver AI-ready data and increase the effectiveness of your data governance programs
Accelerate data use
Enforce policies in real-time
Automate policy enforcement at machine speed, ensuring compliance without slowing down AI, analytics, and data initiatives.
Ensure purpose-based policies
Use the purpose of data use as a consistent input for data governance policy application, starting at project initiation.
Snowflake and OneTrust: Balance accountability and responsible data use with innovative consent management, data and AI governance, and data privacy solutions.
Remove data use bottlenecks created by manual data governance practices
Our Data Use Governance™ solution is built for modern, AI-driven data environments. We designed the solution to favor policy-centric over data-centric governance, programmatic over manual enforcement, and project-initiated over access-based data enablement. Scalable by design, it lays the foundation for efficient and reliable data governance across your organization.
Capture the context of your data for machine scalable decisions
Use advanced, AI-driven data classification techniques on both structured and unstructured data sources to capture data context for both human and machine understanding of your data. Accurate classification enables machine enforceable data policies. OneTrust uniquely supports classification using four contexts — business, regulatory, consent, and data — ensuring data is used appropriately.

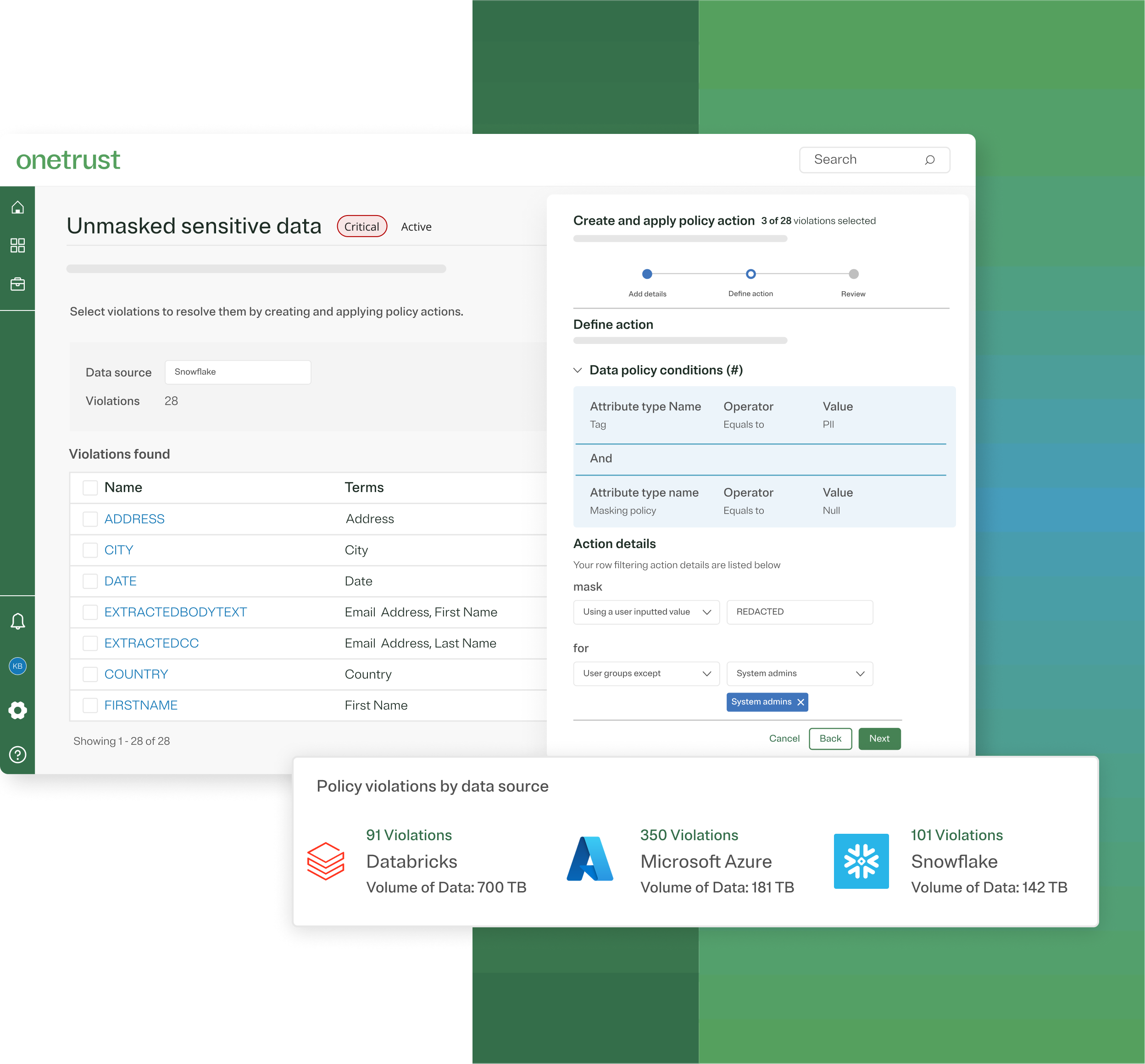
Turn documented data policies into enforceable control code
Combine your privacy, consent, and regulatory data policies in one place for streamlined policy enforcement. Manage data policies for the full lifecycle of data—from ingestion and usage to sharing—ensuring transparency and compliance throughout.

Connect data policies directly to real-time data controls native to your modern data & AI systems
Shift from policy attestation to proactive enforcement of data use with automated data controls. The OneTrust interface tracks the connection between policy documentation and control enforcement to minimize governance bottlenecks and provide transparency.
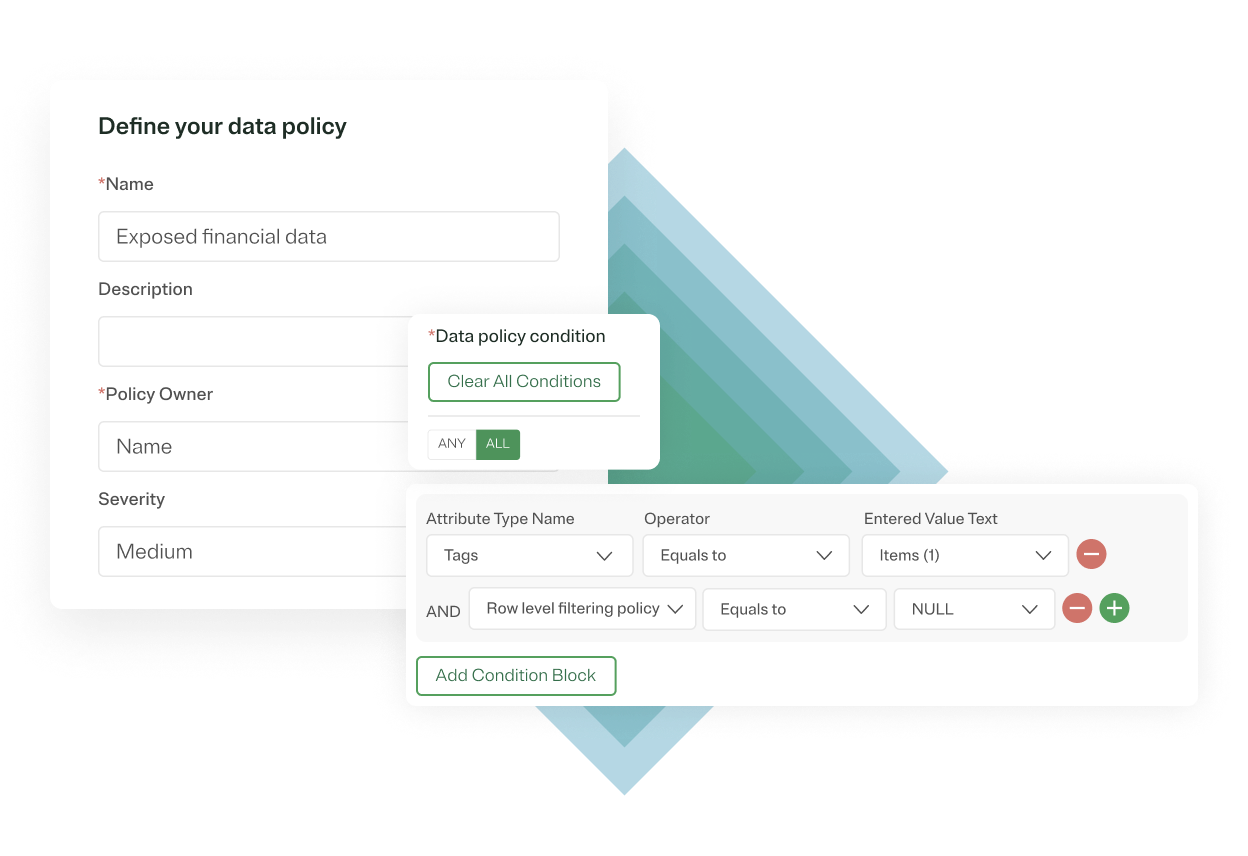
Audit the application of column masking & row-filtering data controls
Ensure accurate enforcement of your data policies by gaining visibility into where column masking and row-filtering policies have been applied in real-time. OneTrust pushes policy logic down through cloud data platforms like Snowflake or Databricks for native data control enforcement. This enables you to use your infrastructure provider’s audit logs to track the last mile execution of controls for compliance.
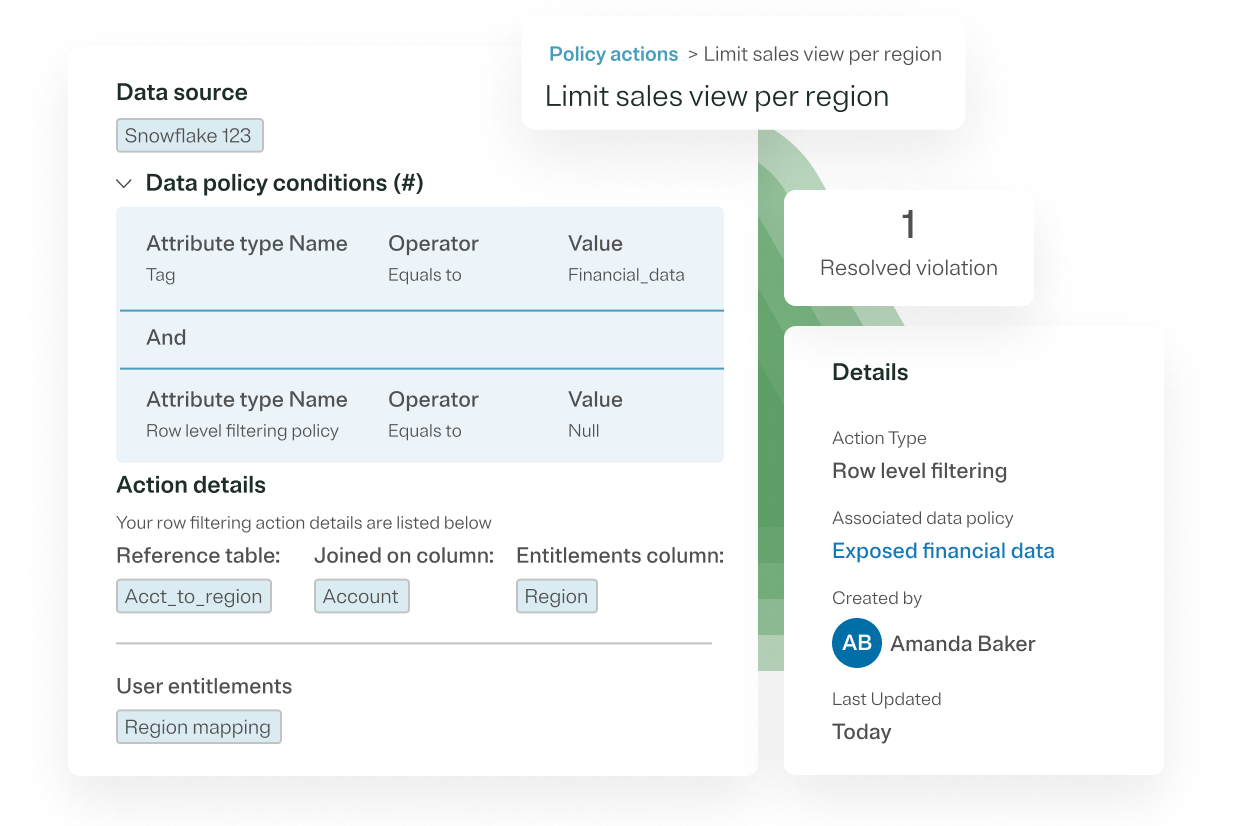
Proven results
Partnering with the best
Our Data Use Governance™ service partners and seamless technology partner integrations make it even easier for you to govern and use your data.
Service partners:



Technology partners:



You may also like
White Paper
Data Use Governance
AI redefines the governance of data based on use
Download our whitepaper and learn how to scale data governance for AI-ready data with programmatic data policies, automated data controls, and embedded data policy enforcement.
May 08, 2025

Blog
Data Use Governance
Empower data governance teams with policy enforcement
OneTrust introduces its approach to delivering insights quickly while ensuring compliance
May 07, 2025 5 min read

Webinar
Data Use Governance
The new data landscape: Navigating the shift to AI-ready data
This webinar will explore the how AI is affecting the data landscape, focusing on how data teams can extend common data practices to support AI’s unique use of data.


