Streamline compliance with 55+ ready-to-action frameworks, prescriptive content, and evidence requirements broken down into measurable tasks.
Tech Risk & Compliance
Simplify compliance and manage risk with confidence
Scale your resources and optimize your risk and compliance lifecycle across a complex technology landscape.
Automate framework compliance
Streamline business collaboration
Connect teams with 200+ pre-built integrations, a user-friendly portal, and automated workflows designed to expedite remediation.
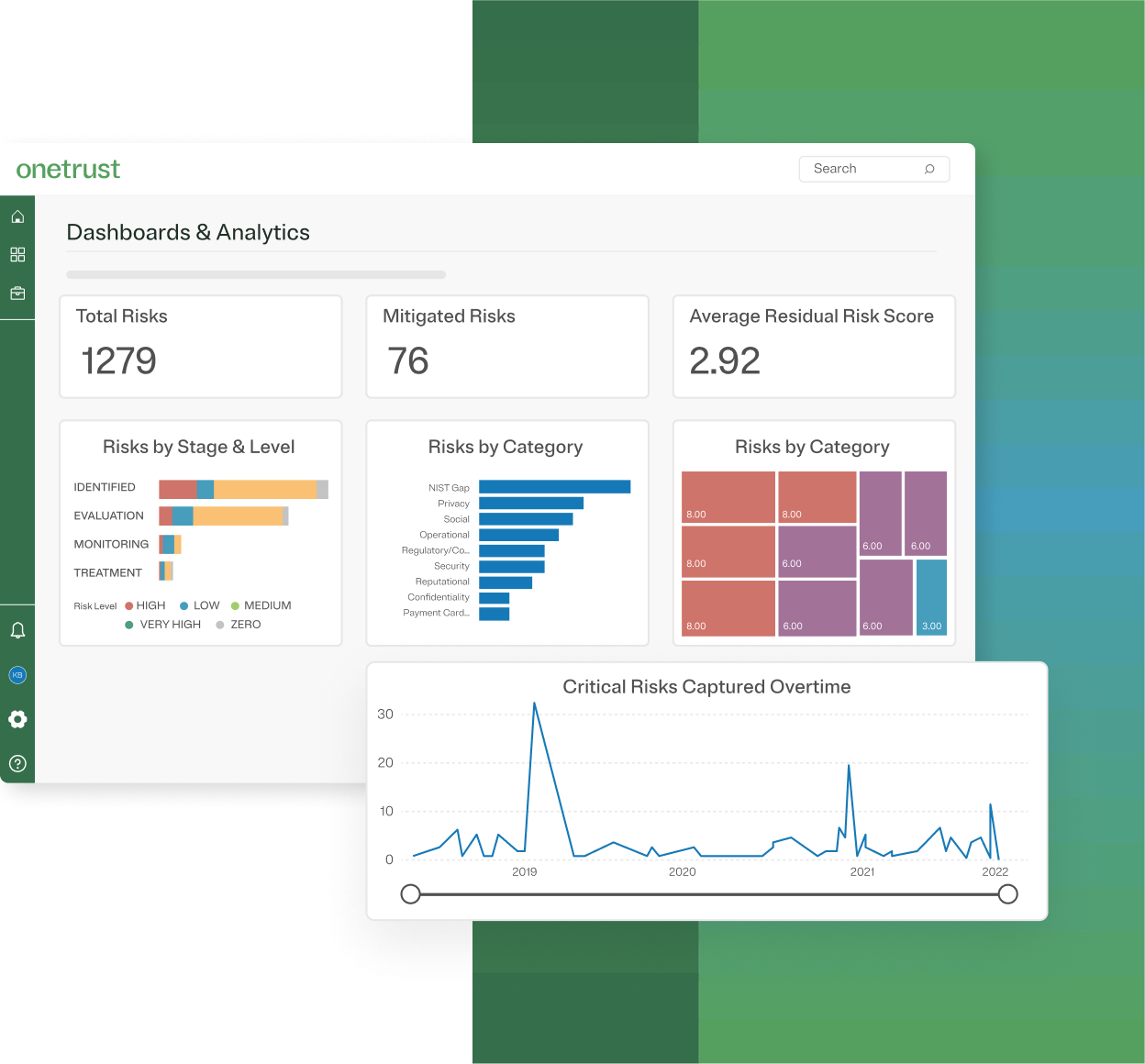
Gain enterprise-wide risk awareness
Map systems, data, and risks in one view. Prioritize action with dynamic scoring and strategic impact insights.
Understand the impact of automation on your organization’s security
Scope your compliance program
Enable scalable, audit-ready compliance for InfoSec and IT teams by efficiently scoping your compliance responsibility.
KEY CAPABILITIES
Initiate a scoping survey to understand compliance responsibility and areas of overlap
Save time with ready-to-use standardized frameworks and a control library for evidence collection tasks


Efficiently manage your compliance program
Eliminate the guesswork of control design and streamline evidence collection across the business to automate governance, risk, and compliance (GRC).
KEY CAPABILITIES
Centralize your compliance processes and automatically generate required controls and evidence tasks based on your operations with insights across 300 jurisdictions
Collect once, comply across 50+ frameworks with our proprietary shared evidence framework
Streamline your policy, risk, and control review processes with robust workflows and automation rules
Monitor and mature your program
Review trends and performance to measure, evaluate, and communicate your compliance posture.
KEY CAPABILITIES
Automate reporting with dynamic, real-time dashboards
Promote a culture of self-reporting with expanded risk and incident intake options
Drive enterprise visibility with ease and quickly establish integrations with our visual builder or access the integrations gallery with 500+ pre-built system connectors

Identify, assess, and prioritize risk mitigation
Automate the mapping of systems, data, and risk flowing throughout your internal and external enterprise.
KEY CAPABILITIES
Maintain an evergreen asset inventory
Leverage flexible risk aggregation and scoring
Build logic into your risk assessment to automate the translation of first-line business information to second-line risk and control identification


Identify, remediate, and report issues and incidents
Manage issue and incident response workflows — from intake through remediation.
Empower enterprise-wide GRC
Eliminate data lags and increase adoption with an intuitive experience for light and heavy users alike.
KEY CAPABILITIES
Engage non-compliance stakeholders with measurable evidence tasks
Integrate directly with your tech stack to automate evidence collection with pre-architected collectors
Simplify configuration updates without the need for IT resources with UI-driven configuration


Centralize policy information and track approvals
Provide employees with a single portal for policy access, reporting, and attestation — while maintaining audit-ready version control and approval workflows.
KEY CAPABILITIES
Build a policy development and approval workflow to reflect your unique process including existing terminology, phases, and reviewers
Generate evergreen policy links to maintain the latest version across private and public-facing domains
Track policy attestations & exceptions with automated follow-up
Featured products
Compliance Automation
Improve compliance visibility across frameworks and business scopes with continuous controls monitoring
Learn moreIT Risk Management
Map, measure, and action IT risk in real-time to scale your risk management programs
Learn moreProven results

"We were able to map the assessment of not only cyber risk but also of many other types of risks – such as compliance."
Nunzio Bucello, CISO, Sara Assicurazioni
"OneTrust GRC capabilities have continually been enhanced and even more so with AI. While the platform is very comprehensive, integrating ML and AI continues to make OneTrust a solid platform for cross-organizational GRC."
75%
Productivity boost
“OneTrust customers recognize up to 75% in productivity enhancements based on process automation."
Partnering with the best
Our Tech Risk & Compliance service partners and technology partner integrations make it even easier for you to scale your resources and automate compliance.
Service partners:



Technology partners:



You may also like
Learn more about our Tech Risk & Compliance packaged service
FAQ
Yes. Your third-party relationships are a reflection of your organization, which means effective enterprise risk management must extend beyond the walls of your organization. Our Third-Party Management solution streamlines every stage of the vendor lifecycle by automating workflows, like onboarding and ongoing vulnerability assessments, and mitigating risk across your portfolio.



