Click to download a free copy of our GRC automation survey summary.
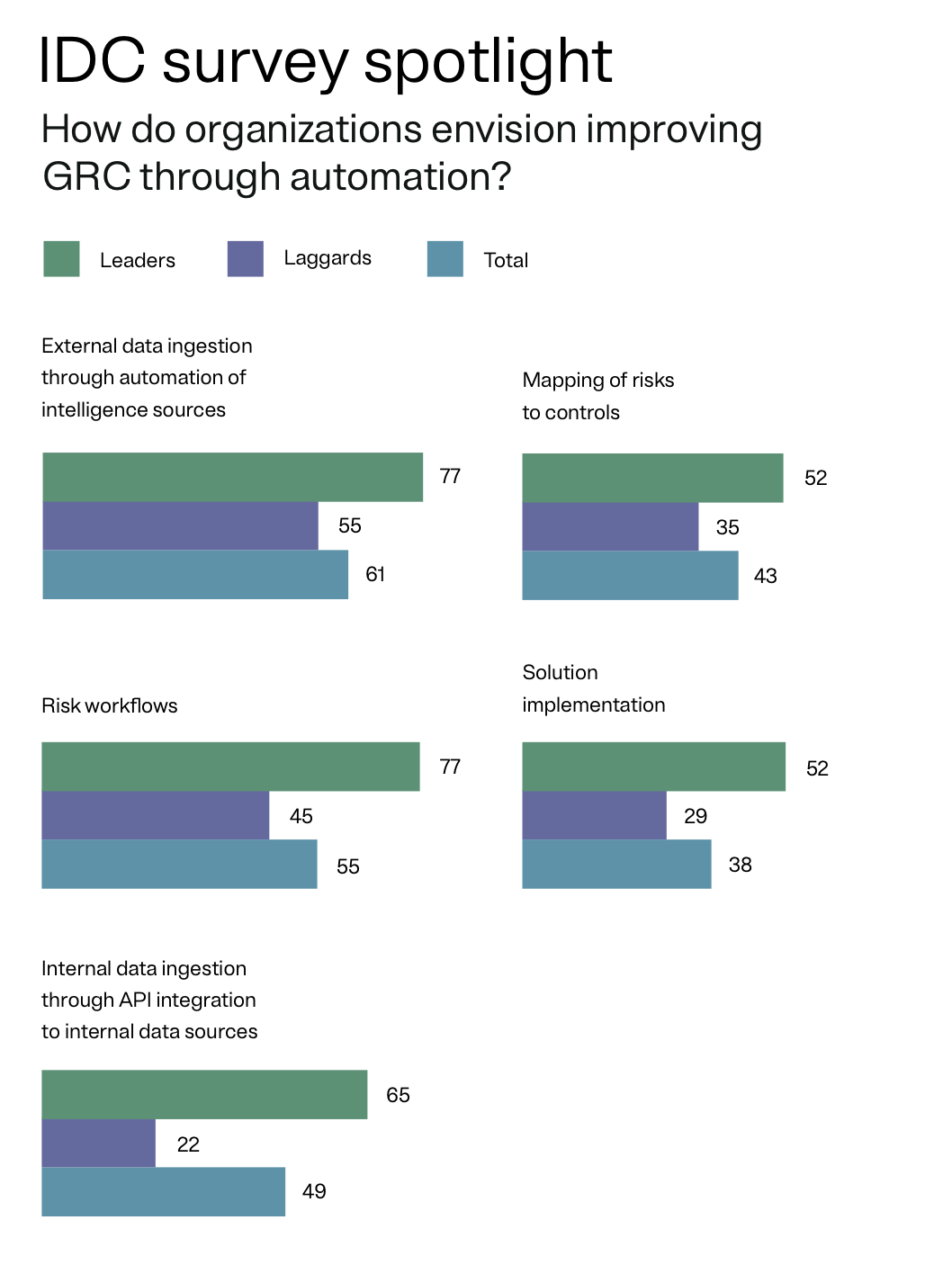
1. External data ingestion through automation of intelligence sources
External data is essential to provide context for a complete view of compliance efforts. Organizations need better risk insights across their vendors and third-party providers, for example, should be able to access critical third-party information and get automatic updates whenever their security, privacy, and compliance posture changes.
2. Risk workflows
Effective GRC programs are the result of collaborative company-wide efforts. Unfortunately, traditional risk workflows do not extend to the business, and assignments to collect insights are often regarded as disruptions to core job responsibilities. This results in employees who are disengaged from the process and program objectives.
A recent survey by VentureBeat found that up to 30% of employees are unfamiliar with their role in cybersecurity.
GRC leaders need modern solutions to automate evidence collection and facilitate intuitive compliance interactions. By reducing friction for everyday business stakeholders, program managers are able to foster a risk-based culture that makes data actionable and ensure processes are audit-ready.
3. Internal data ingestion through API integration
Businesses today rely on an increasing number of software applications, each with its own method of data collection and storage.
Applications can be configured to share data across internal sources using open API integrations. However, most integration opportunities require significant resources to scope, build, and maintain connectivity every time the system is updated. Oftentimes, reverting to traditional assets can be a more attractive option compared to taking on potential tech debt.
Technology vendors that offer purpose-built integrations for common customer use cases help leading companies promote GRC program adoption, better data hygiene, and greater solution value at scale.
4. Mapping risks to controls
Control mapping is the foundation of a strong GRC program, offering visibility into the organization’s overall risk environment. By aggregating controls and their associated risks — creating a single source of truth — mapping controls helps effectively identify areas of interconnected risk and control gaps that would otherwise result in risk blind spots.
Leaders need solutions that provide actionable insights and help them make data-driven decisions, as they evaluate their existing execution against strategic GRC initiatives.
5. Solution implementation
CISOs today are expected to secure every digital aspect of an enterprise, with their area of responsibility expanding into all areas of technology operations. To meet these needs and respond quickly to requirement changes or security incidents, leaders need out-of-the-box connectivity. Solutions that can offer pre-configured integrations, intuitive compliance interactions, and actionable insights that help make data-driven decisions will help set the foundation for continuous compliance.
About OneTrust Compliance Automation
OneTrust Compliance Automation helps you navigate changes within the information security landscape and stay ahead of compliance requirements.
With simplified security standards, automated scoping wizards, and a proprietary shared evidence framework, our integrated platform can fast-track your audit process enable you to test once, comply many.
Reduce your cost of compliance up to 60% and obtain certifications 50% faster.
Get a demo to learn more about how OneTrust Compliance Automation helps you build, scale, and automate your security compliance program.