Data discovery has as much to do with classifying its whereabouts and importance as it does what actions should ultimately be taken with that digital information. Forward-looking security should employ the shift left data strategy. But what exactly does that mean?
Shift left: A data classification strategy
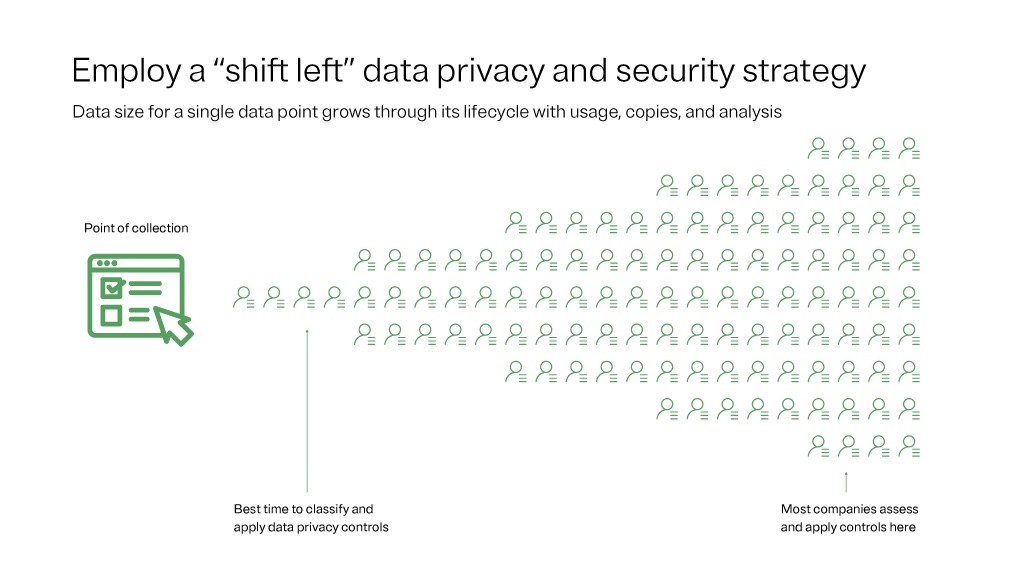
Shift left is a philosophy that looks to catalog, classify, and govern data at data ingestion or creation (at the left side of a horizontal funnel that illustrates the data lifecycle and its proliferation — see image). According to IAPP, that narrow end represents the point when data first enters the company’s tech ecosystem. As you move right in the funnel, the amount of data grows with copies, inferences, and data analysis. The point of collection is best suited to classify and inventory data, so that it follows the data, creating downstream efficiencies. Most companies classify and inventory data toward the right side of the funnel, which is a recipe for delays, inaccuracies, and potential security incidents.