Streamline compliance with 55+ ready-to-action frameworks, prescriptive content, and evidence requirements broken down into measurable tasks.
Tech Risk and Compliance
Simplify compliance and effectively manage risks
Scale your resources and optimize your risk and compliance lifecycle.
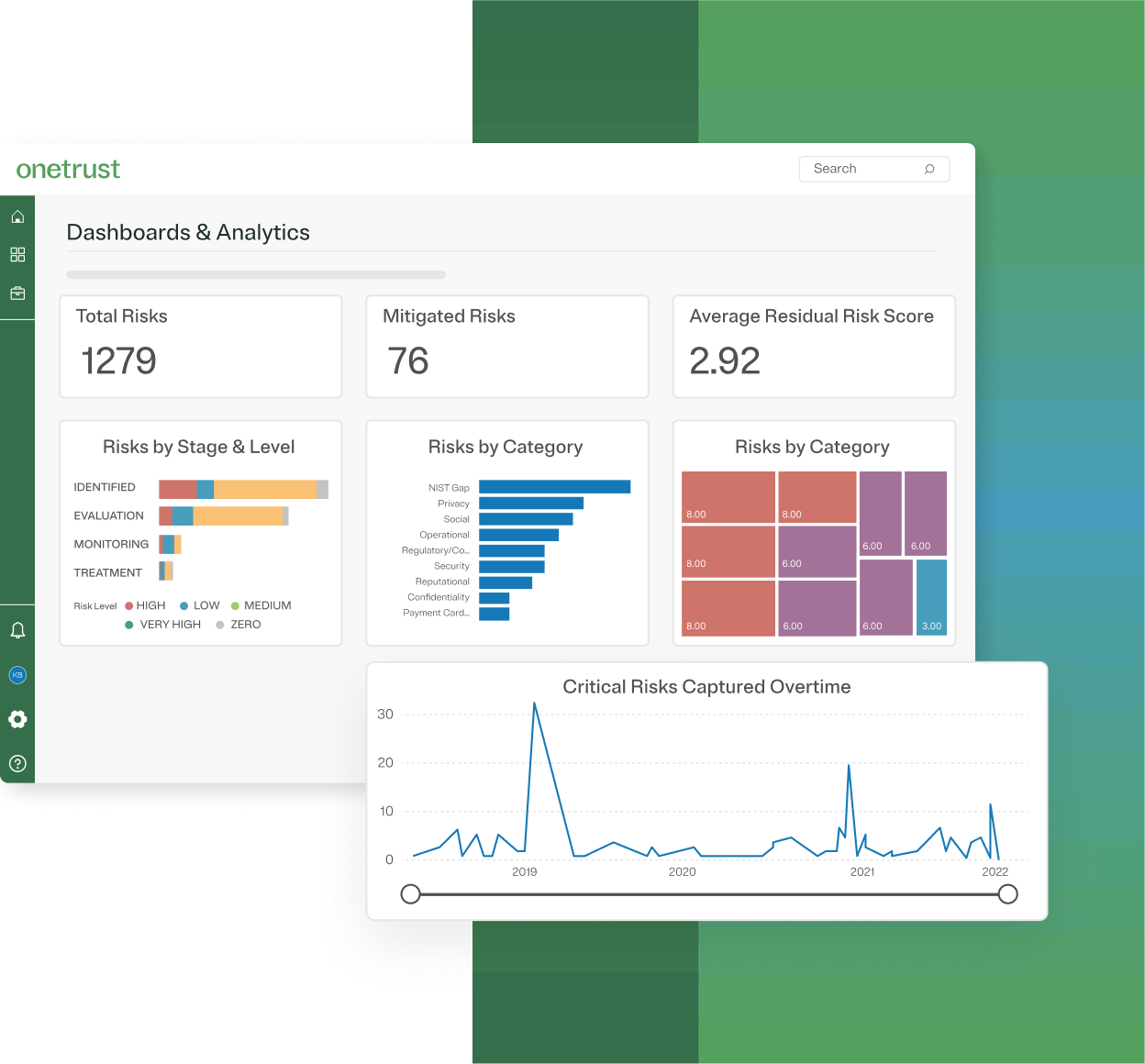
Automate framework compliance
Streamline business collaboration
Connect teams with 200+ pre-built integrations, a user-friendly portal, and automated workflows designed to expedite remediation.
Gain enterprise-wide risk awareness
Map systems, data, and risks in one view. Prioritize action with dynamic scoring and strategic impact insights.
Understand the impact of automation on your organization’s security
Scope your compliance program
Enable scalable, audit-ready compliance for InfoSec and IT teams by efficiently scoping your compliance responsibility.
KEY CAPABILITIES
Initiate a scoping survey to understand compliance responsibility and areas of overlap
Save time with ready-to-use standardized frameworks and a control library for evidence collection tasks


Efficiently manage your compliance program
Eliminate the guesswork of control design and streamline evidence collection across the business to automate governance, risk, and compliance (GRC).
KEY CAPABILITIES
Centralize your compliance processes and automatically generate required controls and evidence tasks based on your operations with insights across 300 jurisdictions
Collect once, comply across 50+ frameworks with our proprietary shared evidence framework
Streamline your policy, risk, and control review processes with robust workflows and automation rules
Monitor and mature your program
Review trends and performance to measure, evaluate, and communicate your compliance posture.
KEY CAPABILITIES
Automate reporting with dynamic, real-time dashboards
Promote a culture of self-reporting with expanded risk and incident intake options
Drive enterprise visibility with ease and quickly establish integrations with our visual builder or access the integrations gallery with 500+ pre-built system connectors

Identify, assess, and prioritize risk mitigation
Automate the mapping of systems, data, and risk flowing throughout your internal and external enterprise.
KEY CAPABILITIES
Maintain an evergreen asset inventory
Leverage flexible risk aggregation and scoring
Build logic into your risk assessment to automate the translation of first-line business information to second-line risk and control identification


Identify, remediate, and report issues and incidents
Manage issue and incident response workflows — from intake through remediation.
Empower enterprise-wide GRC
Eliminate data lags and increase adoption with an intuitive experience for light and heavy users alike.
KEY CAPABILITIES
Engage non-compliance stakeholders with measurable evidence tasks
Integrate directly with your tech stack to automate evidence collection with pre-architected collectors
Simplify configuration updates without the need for IT resources with UI-driven configuration


Centralize policy information and track approvals
Provide employees with a single portal for policy access, reporting, and attestation — while maintaining audit-ready version control and approval workflows.
KEY CAPABILITIES
Build a policy development and approval workflow to reflect your unique process including existing terminology, phases, and reviewers
Generate evergreen policy links to maintain the latest version across private and public-facing domains
Track policy attestations & exceptions with automated follow-up
Featured products
Compliance Automation
Improve compliance visibility across frameworks and business scopes with continuous controls monitoring
Learn moreIT Risk Management
Map, measure, and action IT risk in real-time to scale your risk management programs
Learn moreProven results

"We were able to map the assessment of not only cyber risk but also of many other types of risks – such as compliance."
Nunzio Bucello, CISO, Sara Assicurazioni
226k
Risks mitigated annually
On average, OneTrust Tech Risk & Compliance customers mitigated 226,000 risks per year.
75%
Productivity boost
“OneTrust customers recognize up to 75% in productivity enhancements based on process automation."
Partnering with the best
Our Tech Risk & Compliance service partners and technology partner integrations make it even easier for you to scale your resources and automate compliance.
Service partners:



Technology partners:



You may also like

Webinar
Responsible AI
Building AI governance with security at the center
Discover how security leaders are securing AI models, data, and infrastructure while driving risk-aware AI governance programs.
July 10, 2025

Webinar
Technology Risk & Compliance
Unifying third-party and tech risk in an AI-driven world
Join our webinar to learn how risk and security leaders are aligning third-party and tech risk for scalable, AI-ready compliance programs.
July 08, 2025

Webinar
Technology Risk & Compliance
Taming compliance complexity: Strategies for scaling across frameworks, systems & geographies
Discover how to scale compliance programs amid rising regulations and complexity. Gain actionable strategies to streamline controls, audits, and global oversight.
June 24, 2025

Webinar
Technology Risk & Compliance
The automation advantage: Unlocking ROI from risk and compliance
Learn how automation reduces compliance costs, boosts audit readiness, and delivers 75%+ time savings across the compliance lifecycle in this practical, ROI-focused session.
May 28, 2025

Webinar
Privacy Management
OneTrust Spring Release
We explore the latest release which introduces AI-assisted features that help privacy and third-party risk teams scale by reducing manual effort and friction, so they can focus on the work that matters most.
May 27, 2025

eBook
Technology Risk & Compliance
The risk-resilient enterprise: Automating compliance for security & scale
Risk flows throughout your organization’s systems and data, and without mapping or monitoring, your company’s security posture is constantly under pressure.
April 24, 2025

Webinar
Technology Risk & Compliance
From reactive to resilient: Building and scaling a modern enterprise risk program
Join our masterclass for CISOs & InfoSec leaders to build scalable, modern risk management programs. Gain actionable strategies, frameworks, and real-world insights for success.
April 22, 2025

Webinar
Technology Risk & Compliance
Harmonizing risk and compliance: Unifying InfoSec programs through automation
Join this webinar to discover how to streamline ISO 27001, GDPR, NIST & PCI DSS with automation, reduce manual work and enhance oversight.
April 09, 2025

Infographic
Technology Risk & Compliance
Automating compliance mitigates risk
Download our infographic to learn steps involved in compliance automation and how it mitigates risk in your organization's security program.
March 27, 2025

Webinar
Technology Risk & Compliance
Operational resilience in a changing world: Going beyond compliance
Join this session to unpack key regulations, such as ISO 27001, APRA CPS 230, DORA, & SOC2, to learn how they impact internal & third-party operations.
February 20, 2025

Webinar
Technology Risk & Compliance
Compliance Automation product showcase
Join our live demonstration and see how Compliance Automation can help boost compliance efficiency with automated workflows, shared evidence, and 40+ frameworks.
December 19, 2024

Webinar
Technology Risk & Compliance
The PDPL in Saudi Arabia is now in effect: is your business ready?
Join our Saudi Arabia PDPL webinar for an overview on the data protection law, its requirements, and how to prepare for full enforcement.
December 12, 2024

Webinar
Technology Risk & Compliance
Elevating client compliance with OneTrust Automation: Key strategies for partners
Discover how to use OneTrust Compliance Automation to establish client baselines, improve efficiency, and drive scalability. Learn key strategies to enhance your compliance impact.
December 11, 2024

Webinar
Technology Risk & Compliance
Understanding the NIS 2 Directive: Compliance insights and best practices
This DataGuidance webinar explores the latest and expected developments in the implementation of the NIS 2 Directive, focusing on practical compliance strategies to ensure your organization is prepared.
December 04, 2024

Webinar
Technology Risk & Compliance
Tech risk and compliance masterclass: An evidence-based approach to building by-design risk and compliance practices
Discover strategies to embed compliance and risk management into business processes with minimal disruption, using technology-driven solutions for efficiency, scalability, and improvement.
November 06, 2024

Webinar
Technology Risk & Compliance
Building a strong security posture: Managing compliance, risk, and business engagement in a dynamic landscape
Join our webinar to learn how to optimize security posture, streamline compliance, and leverage automation to manage IT risk in today's complex digital landscape. Register now!
October 29, 2024

Webinar
Privacy Automation
Build resiliency and operationalize compliance with OneTrust: Fall product release recap, 2024
Join our upcoming product release webinar to explore how these new capabilities can help your organization navigate complex frameworks, streamline third-party management, and accelerate AI and data innovation.
October 22, 2024

Webinar
Technology Risk & Compliance
Tech risk & compliance masterclass: The anatomy of a framework
Master the fundamentals of constructing robust compliance frameworks that can seamlessly integrate with organizational operations while aligning with regulatory and strategic mandates to deliver measurable insights on your progress and gaps.
August 14, 2024

Webinar
Third-Party Risk
Third-Party Risk Management: From compliance to strategy
Navigate third-party risk challenges and discover strategic steps to scale, automate, and operationalize your program with this webinar series.
August 09, 2024

Webinar
Technology Risk & Compliance
Tech risk and compliance masterclass
Unlock tech risk management & compliance excellence. Master risk management, build robust frameworks, and foster cross-functional collaboration for long-term resilience.
August 07, 2024

Webinar
Technology Risk & Compliance
Introducing OneTrust Compliance Automation
Join us as we explore OneTrust Compliance Automation, a holistic and fully integrated solution that streamlines and optimizes workflows, compliance, and attestation.
July 25, 2024

Webinar
Data Discovery & Classification
Catch it live: See the all-new features in OneTrust's Spring Release and Post-TrustWeek recap
Join us as Ryan Karlin, Senior Director of Product Marketing highlights important updates from TrustWeek including an inside look into OneTrust's new platform features that make it easier for customers to activate data responsibly, surface and mitigate risk, and navigate the complex regulatory environment.
June 06, 2024

Report
AI Governance
GRC strategies for effective AI Governance: OCEG research report
Download the full OCEG research report for a snapshot of what organizations are doing to govern their AI efforts, assess and manage risks, and ensure compliance with external and internal requirements.
May 22, 2024

Infographic
Third-Party Risk
Streamline compliance with the Digital Operational Resilience Act (DORA)
Download our infographic to learn about the new DORA regulation, who needs to comply, and how OneTrust can help streamline the process.
April 29, 2024

Webinar
Ethics Program Management
EthicsConnect: Risk - It’s not just for breakfast anymore
Join us for a deep dive into embedding privacy by design into the fabric of your business to promote the responsible use of data.
April 25, 2024

Infographic
Technology Risk & Compliance
Rethinking risk assessments: Bridging the gap between best practices and action
Download our infographic to learn the main challenges faced during risk assessments, proven frameworks for assessing risks, and how to translate guidance into action.
March 07, 2024

Webinar
Technology Risk & Compliance
PCI DSS Compliance: How to scope and streamline monitoring with Certification Automation
Join our PCI DSS webinar where we discuss how Certification Automation can help free up valuable InfoSec resources, streamline audits, and stay continuously compliant.
March 05, 2024

eBook
Ethics Program Management
Business messaging apps: A guide to corporate compliance
How can your business use third-party messaging apps while staying compliant? Dive into key usage considerations based on the DOJ’s 2023 guidance.
February 13, 2024

Webinar
Technology Risk & Compliance
5 automation trends to modernize InfoSec compliance
Join our webinar for insights on transforming InfoSec program management. Navigate the complexities of modern security with a flexible, scalable, and cost-effective approach.
February 07, 2024

Infographic
Third-Party Risk
4 top-of-mind challenges for CISOs
What key challenges do CISOs face going into the new year? Download this infographic to hear what experts from industries across the board have to say.
January 30, 2024

eBook
Technology Risk & Compliance
NIST CSF 2.0: Changes, impacts and opportunities for your Infosec program
Get your free guide to the NIST Cybersecurity Framework 2.0 and learn how its proposed changes will impact your InfoSec programs.
December 18, 2023
Resource Kit
Technology Risk & Compliance
NIST CSF essentials: Empowering cybersecurity excellence
Download our NIST CSF Essentials resource kit and master cybersecurity compliance with expert insights, strategies, and real-world case studies.
December 15, 2023

Webinar
Technology Risk & Compliance
Demonstrating GDPR compliance with Europrivacy criteria: The European Data Protection Seal
Join our webinar to learn more about the European Data Protection Seal and to find out what the key advantages of getting certified.
November 30, 2023

Data Sheet
Technology Risk & Compliance
Integrations to automate your framework compliance: ISO 27001, SOC 2, and NIST CSF
Explore how OneTrust integrations can help you automate compliance with today’s most popular InfoSec frameworks.
November 28, 2023

Checklist
Technology Risk & Compliance
SOC 2 checklist: 8 steps to achieve compliance
This SOC 2 checklist provides clear action steps that enable you to mature your security program and fast-track your way to compliance.
November 28, 2023

Webinar
Ethics Program Management
Ethics Exchange: Risk assessments
Join our risk assessments experts as we discuss best practices, program templates, and how provide an assessment that provides the best value for your organization.
October 25, 2023

Infographic
Technology Risk & Compliance
Understanding Europe's Top InfoSec and Cybersec Frameworks
Learn the ins and outs of Europe’s top InfoSec and cybersec frameworks, including ISO 27001, UK Cyber Essentials, the NIS2 Directive, DORA, and more.
October 05, 2023

Infographic
Technology Risk & Compliance
5 key areas for improved automation in InfoSec compliance
Streamline and scale your organization’s InfoSec compliance program by focusing on these five key areas of automation.
October 02, 2023

eBook
Technology Risk & Compliance
Prioritizing the right InfoSec frameworks for your organization
In this free eBook, we explore the basics of three top InfoSec frameworks and how to decide which is the best fit for your organization.
September 27, 2023

Webinar
Third-Party Risk
Live Demo EMEA: How OneTrust can help advance your third-party risk management program
Join us for a live demo of OneTrust's third-party risk management solution and see how it can help automate and streamline your TPRM program.
September 19, 2023

eBook
Privacy Management
Responsible data use: Navigating privacy in the information lifecycle eBook
Download this eBook and get the insights you need to safeguard customer privacy and ensure responsible data use in the information lifecycle.
August 22, 2023

Webinar
Technology Risk & Compliance
How to successfully implement ISO 27001 to demonstrate security and assurance across any jurisdiction
Join our live webinar and hear from security professionals on how to get ISO 27001 certified, streamline audit preparation, and demonstrate security assurance across any regulatory jurisdiction.
June 28, 2023

eBook
Third-Party Risk
InfoSec's guide to third-party risk management: Key considerations and best practices
Download our eBook to learn practical advice on how to approach third-party risk management like an InfoSec expert.
June 05, 2023

Webinar
GRC & Security Assurance
Combating InfoSec compliance fatigue: Insights for navigating growingly complex requirements
In this webinar, you will hear first-hand from information security experts experts what are the key pain-points and their strategies to be audit ready.
February 27, 2023

Webinar
Technology Risk & Compliance
Introducing OneTrust Certification Automation: Build, scale, and automate your InfoSec compliance program webinar
In this webinar, learn how to right-size your compliance scope for different frameworks across various business dimensions and enable an agile audit process.
February 15, 2023

Webinar
GRC & Security Assurance
Introducing OneTrust Certification Automation: Reinforce privacy accountability with automated InfoSec compliance
Learn how to enable an agile audit process by breaking down complex InfoSec requirements into actionable tasks to help automate your compliance program.
February 10, 2023

eBook
Technology Risk & Compliance
The future of information security
Learn how to respond to the security landscape and build a proactive InfoSec program to help your customers and business.
October 10, 2022

eBook
Technology Risk & Compliance
The art of the enterprise IT risk assessment
Ensure your enterprise IT risk assessment is a success with a top-down approach that gets executive buy-in from the start
September 16, 2022

eBook
Technology Risk & Compliance
The enterprise DevSecOps playbook
As a unified business function, DevSecOps combines rapid software development with top-notch security at scale.
September 02, 2022

Webinar
GRC & Security Assurance
How to reinforce your InfoSec risk program in a “Not If, But When” incident environment webinar
Learn how scaling your approach to managing IT assets & risk assessments can deliver a complete picture to better measure and inform program investments.
August 16, 2022

Webinar
GRC & Security Assurance
5 critical mistakes to avoid when answering security questionnaires
Avoid these 5 critical mistakes when answering security questionnaires and streamline responses with this webinar.
March 01, 2022

Webinar
GRC & Security Assurance
How successful security teams manage risk to build Trust and drive Growth
Watch this webinar to learn what makes a successful risk management program and how effective security teams build trust.
January 12, 2022

Webinar
Privacy Management
Build an incident management playbook
Prepare for privacy and security incidents by building an incident management playbook.
August 27, 2021
Fundamental to Comprehensive: Where Does Your Compliance Program Stand? Infographic | Resources | OneTrust

Demo
Technology Risk & Compliance
OneTrust Tech Risk and Compliance demo
Manage tech risks and ensure compliance with our all-in-one solution. Automate workflows, scale resources, and measure program effectiveness to stay ahead of evolving regulations.
Learn more about our Tech Risk & Compliance packaged service
FAQ
Yes. Your third-party relationships are a reflection of your organization, which means effective enterprise risk management must extend beyond the walls of your organization. Our Third-Party Management solution streamlines every stage of the vendor lifecycle by automating workflows, like onboarding and ongoing vulnerability assessments, and mitigating risk across your portfolio.
