Simplify compliance, improve operational efficiency, and enable risk-informed decisions.
Privacy Operations
Simplify privacy compliance
Operationalize privacy program activities to manage risk, demonstrate accountability, and meet regulatory requirements.
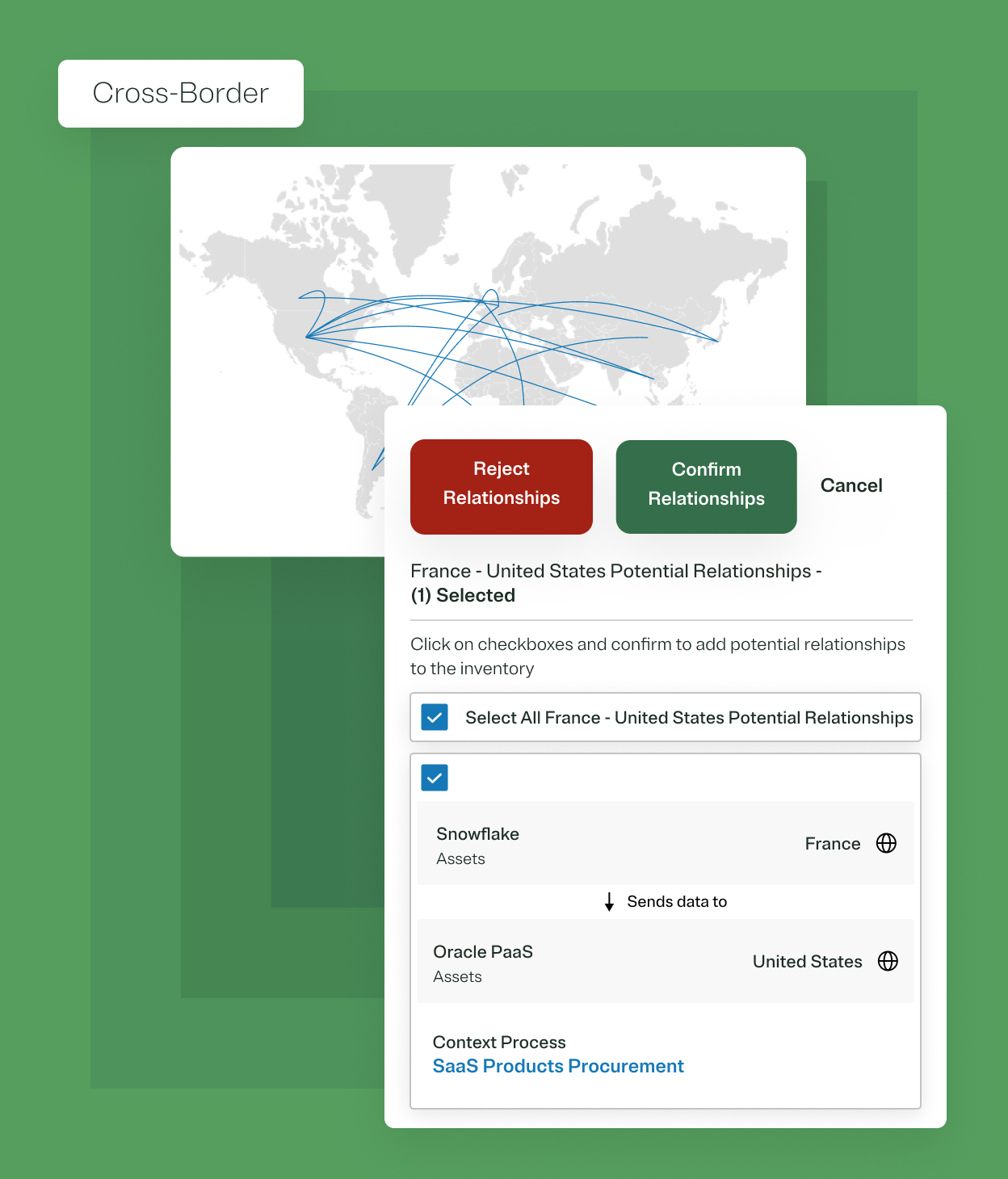
Connect to data assets to detect personal data, automate recordkeeping, monitor risk posture, and trigger remediation.

Get a central view into your personal data processing across your data assets, processing activities, and vendors to auto-generate record of processing activities (RoPA), identify data transfers, and manage privacy posture.

Automate privacy impact, vendor, and AI risk assessments (PIA, DPIA, TIA, etc.) and manage risk mitigation workflows.

Manage incident response workflows and get automated notification guidance per jurisdiction.

Pre-populate notice sections with real-time OneTrust data (e.g. cookie table) and easily publish updates across multiple websites and apps.

Do more with OneTrust Privacy Automation

“OneTrust exponentially grew my team's bandwidth. I'd estimate that we're now operating as if we had four to five more people than we do.”
Director of Digital Trust, Pharmaceuticals
Source: Forrester Total Economic Impact™ study
Explore related resources

Privacy Automation
Optimize privacy operations: Scale and manage risks effectively
This session will explore strategies for scaling privacy automation and risk management as well as overcoming compliance and automation challenges.
July 17, 2025

Privacy Management
OneTrust Using OneTrust: Managing data privacy
Learn how how our Privacy department leverages OneTrust's tools to automate privacy workflows, ensuring compliance and efficiency.
July 16, 2025

Privacy Automation
Global regulatory update: 2025 privacy trends & what to watch next
Join OneTrust for a live mid-year update on the key privacy trends and regulatory shifts defining 2025. With intelligence from OneTrust DataGuidance, you’ll walk away with a clear view of where regulation is heading and how to stay ahead in a year of constant change.
July 09, 2025

Privacy Automation
Navigating EO 14117: A roadmap for compliance and risk mitigation
Join experts from OneTrust, KPMG, and Hogan Lovells for a timely webinar designed to help you navigate the complexities of Executive Order 14117 and the DOJ’s recent guidance.
July 08, 2025

Privacy Automation
Strengthen your privacy & AI governance strategy with OneTrust DataGuidance
In this live demo, learn how OneTrust DataGuidance helps you reduce research time, minimize external counsel costs, and confidently meet global compliance requirements at scale.
June 30, 2025

Privacy Automation
Philippines' PDPA compliance: What you need to know
The Philippines' Personal Data Protection Act was established to uphold the right to privacy and ensure organizations manage personal data with care, transparency, and accountability.
June 27, 2025

AI Governance
Bringing privacy to the AI table with data protection by design
Join our webinar to see how privacy professionals are embedding compliance and trust into AI governance programs from the start.
June 24, 2025

Privacy Automation
Automating privacy touchpoints: Notices, consent, and DSRs made easy
Join us and learn how to simplify and scale privacy compliance by automating key consumer touchpoints.
June 12, 2025

Privacy Automation
Live demo: Scale privacy with automation
Join our live demo and see how OneTrust Privacy Automation empowers privacy teams to simplify compliance, reduce manual work, and scale programs efficiently.
May 29, 2025

Privacy Management
Celebrating the GDPR's 7th anniversary
Join us as we celebrate the GDPR's 7th anniversay and discuss the landmark's privacy law's milestones and compliance challenges.
May 28, 2025

Third-Party Risk
Data privacy compliance and Third-Party Risk Management: A unified approach
These days, organizations are required to safeguard their customer data and comply with privacy regulations — a task that becomes even more challenging with the increase in third-party relationships.
May 23, 2025

Privacy Automation
Simplifying Philippines PDPA compliance: A practical guide for privacy professionals
Learn what the Philippines' PDPA requires and get practical steps to build a scalable, privacy-forward compliance program.
May 15, 2025

Privacy Automation
Streamlining compliance: Best practices for privacy automation
Join our webinar as we explore best practices for streamlining compliance through automation, enhancing efficiency and reducing manual effort.
May 13, 2025

Privacy Automation
Scaling privacy: Inside OneTrust’s AI agents and automation
Learn how OneTrust's latest AI innovations, including Privacy AI Agents, are enabling privacy teams to govern effectively and move quickly.
May 01, 2025

Privacy Automation
Driving value through automation: Practical steps to scale your privacy program
Learn how to transition from compliance to scalable automation, enhancing efficiency, reducing risks, and improving compliance outcomes.
April 24, 2025
Responsible AI
You can’t scale privacy without AI: Welcome to the new era of privacy management
Learn how AI agents are transforming privacy operations. Helping teams scale compliance, reduce manual work, and lead with confidence.
April 23, 2025

Privacy Automation
Laying the foundation: The why and how of privacy automation
Join our webinar as we introduce the Data Privacy Maturity Model, explaining its importance in identifying where your organization stands today and how to strategically advance.
April 17, 2025

Privacy Management
NIS2 in practice: Implementation of technical measures
Join experts from Sidley Austin LLP and ENISA for a webinar on the practical implementation of NIS2 technical measures. Gain insights on compliance, technical strategies, and the latest EU legislation to strengthen your NIS2 readiness.
March 20, 2025

Privacy Management
Privacy roadmap 2025: What organizations need to prioritize
Join our webinar, Privacy Roadmap 2025 – What Organizations Need to Prioritize, to explore key privacy trends, regulatory updates, and AI governance challenges
March 04, 2025

Privacy Automation
Turn compliance into your competitive edge with Privacy Automation
This webinar explores the evolving privacy landscape, the future of compliance, and real-world examples of effective privacy automation.
February 27, 2025

Privacy Automation
Navigating the FTC's amended COPPA Rule: Key updates and compliance strategies
This webinar covers key updates to the FTC's amended COPPA Rule. Learn revised privacy notice requirements, verifiable parental consent, governance protocols, and best practices for data retention.
February 25, 2025

Privacy Automation
Live demo: OneTrust Data & AI Governance
Register for this 30-minute live demonstration to see how a data steward and an AI product owner use OneTrust Data & AI Governance.
February 25, 2025
Privacy Automation
OneTrust data privacy maturity self-assessment
Gauge the maturity of your privacy program and identify areas of improvement to further mature your privacy operations.
February 18, 2025

Privacy Automation
IAPP hosted webinar: Discovering the ROI of Privacy Automation
Discover how OneTrust Privacy Automation transforms privacy programs from compliance-focused to strategic assets. Learn how automation maximizes ROI, boosts efficiency, mitigates privacy risks, and drives competitive advantage.
February 06, 2025

Privacy Management
APAC Data Privacy Day 2025
Join us for a special Data Privacy Daty 2025 webinar as we look back on 2024's data protection and privacy trends across Asia Pacific and Japan (APAC), as well as what to expect in the region for 2025.
January 30, 2025

Privacy Automation
OneTrust in Action: Building Seamless and Trusted User Journeys - Live Demo
Learn how to streamline data privacy compliance with OneTrust Consent & Preferences. Build trust, enhance user experience, and align with global regulations through user-driven consent management.
January 29, 2025

Privacy Management
2024 to 2025: Preparing for the next wave of privacy regulations
Prepare for 2025's privacy changes with this recap webinar on 2024's regulations and explore upcoming laws, trends, and compliance strategies.
January 23, 2025

Privacy Management
Your Data Privacy Day handbook
This guide give you a range of information and resources to raise privacy awareness this Data Privacy Day.
January 21, 2025

AI Governance
Overcoming the privacy pitfalls of GenAI (APAC)
Join us and learn about the data privacy risks of adopting GenAI and practical strategies on avoiding them.
January 08, 2025

Privacy Management
Top 10 privacy moments that shaped 2024
In this webinar, DataGuidance privacy analysts will review of privacy enforcement trends in 2024, explore global AI regulations, including the EU AI Act, and discuss global privacy legislation developments in 2024.
December 19, 2024

Privacy Management
Emerging privacy laws in the Northeast: Key insights and compliance strategies
Join our webinar to explore key 2025 data privacy laws in the Northeast US, including New Jersey’s Senate Bill 332, New Hampshire Senate Bill 255, and Rhode Island's Data Data Transparency and Privacy Protection Act.
December 18, 2024

Consent & Preferences
Deliver hyper-personalized experiences with a privacy-first approach to first-party data
Download our infographic to earn how to navigate new privacy laws and deprecating cookies with Adobe CDP and OneTrust.
December 18, 2024

Privacy Automation
Redefining privacy as a business asset: The value of Privacy Automation
This webinar will explore how OneTrust Privacy Automation transforms privacy programs into proactive, business-aligned functions that enhance decision-making and accountability.
December 17, 2024

Cookie Consent
How to handle opt-outs for tracking pixels under Australian privacy law
Join our webinar to learn how to master consent management and handle opt-outs for tracking pixels.
December 12, 2024

Privacy Automation
GDPR: Dos and don'ts
Navigating GDPR compliance can feel daunting, especially for businesses with limited resources. This quick infographic guide of actionable “dos” and “don’ts” will help you develop the foundation of a broader privacy-first approach that keeps you aligned with your GDPR compliance goals.
December 10, 2024

Privacy Automation
Defining a new direction for data
As AI continues to offer unparalleled opportunities for business innovation, it also presents risks that organizations must tackle head-on through scalable governance programs that span multiple data sources. Six key trends are defining these challenges.
November 13, 2024

Privacy Automation
From request to resolution: Simplifying DSRs with automation
Learn how OneTrust's Data Subject Rights (DSR) Automation solution can automate DSRs from intake through fulfillment including ID verification, data detection and deletion, redaction, and secure response.
November 06, 2024

Privacy Automation
Explore the future of regulatory intelligence: A DataGuidance demo
In this live demo webinar, we will showcase the advancements in regulatory intelligence embedded within the DataGuidance platform, which offers comprehensive and updated regulatory research across 300+ jurisdictions.
October 29, 2024

Privacy Automation
Privacy beyond compliance: Driving business value through responsible data use
Learn how to evolve your privacy program beyond compliance and drive business value through the responsible use of data.
October 24, 2024

Privacy Automation
Tackling your key challenges from the ICO Data Protection Practitioner's Conference
Following this year’s ICO Data Protection Privacy Conference, we’re bringing together a panel of leading privacy and data governance experts from the OneTrust Chapter Chair Community to address your most pressing questions.
October 23, 2024

Privacy Automation
Build resiliency and operationalize compliance with OneTrust: Fall product release recap, 2024
Join our upcoming product release webinar to explore how these new capabilities can help your organization navigate complex frameworks, streamline third-party management, and accelerate AI and data innovation.
October 22, 2024

Privacy Automation
Transforming data privacy and governance with OneTrust and Snowflake
OneTrust’s privacy platform, powered by Snowflake, ensures secure data sharing and governance, helping organizations manage privacy without compromising collaboration.
October 18, 2024

Privacy Automation
Privacy automation 101: Simplifying data mapping and risk assessments
Join this webinar to learn how OneTrust helps you automate Data Mapping and Privacy Risk Assessments and how to overcome maintenance challenges.
September 25, 2024

Privacy Automation
Proven ROI with OneTrust
Learn how a composite organization achieved a 227% return on investment over 3 years and payback in just 7 months by leveraging OneTrust to streamline privacy, data governance, and consent management.
September 24, 2024

Privacy Automation
Discover the economic benefits of OneTrust
Download this 2024 Forrester Consulting Total Economic Impact™ study to see how OneTrust has helped organizations navigate data management complexities, generate significant ROI, and enable the responsible use of data and AI.
September 24, 2024

Privacy Automation
Global regulatory update: Recent privacy developments and compliance trends
Join us for a webinar on the latest updates and emerging trends in global privacy regulations.
September 12, 2024

Privacy Management
OneTrust Live: Unlocking the power of automation for privacy programs
Join us for a live demo where we will discuss the advanced capabilities of OneTrust solutions in data privacy enforcement, first-party data collection, and AI innovation.
August 21, 2024

Privacy Management
CPRA in action: OneTrust Live Demo
Join us for a deep dive tour of our suite of technology solutions for operationalizing and automating CPRA requirements across Do Not Share, Consumer Rights and privacy governance operations.
August 01, 2024

Responsible AI
Privacy and AI: Bridging the divide
Watch this webinar for insights on ensuring responsible data use while building effective AI and privacy programs.
July 31, 2024

Privacy Automation
Moving through the Data Privacy Maturity Model
Explore the Data Privacy Maturity Model to evolve your data privacy program from compliance-focused to a strategic, value-driven framework.
July 29, 2024

Technology Risk & Compliance
Introducing OneTrust Compliance Automation
Join us as we explore OneTrust Compliance Automation, a holistic and fully integrated solution that streamlines and optimizes workflows, compliance, and attestation.
July 25, 2024

Privacy Management
Going beyond CCPA
Join us for an in-depth webinar on "Going Beyond CCPA," where we will explore the intricacies of privacy laws, compare major regulations, and provide guidance on enhancing your privacy policy.
July 25, 2024

Privacy Management
The evolution of CCPA
Join us for an insightful webinar on "The Evolution of CCPA" where we will delve into the latest amendments, understand their impact, and explore the new requirements and implications for businesses.
July 18, 2024

Privacy Management
Mastering data privacy: Navigating CCPA, CPRA, and beyond
Mastering Data Privacy: Expert Guidance on CCPA, CPRA, GDPR Compliance, Privacy Policy Best Practices, and Live Demo Insights
July 18, 2024

Privacy Management
OneTrust Live: Complying with US Privacy Laws Effective July 2024
Join us on July 17th for a live demo of OneTrust's solutions, providing you with practical tools and strategies to ensure your organization is compliant with both new and existing data privacy laws in the US.
July 17, 2024

Privacy Management
OneTrust Live: Revolutionizing Your Data Strategy with Enhanced Privacy and AI
Join us for a live demo showcasing the cutting-edge capabilities of OneTrust solutions in the realms of data privacy enforcement, first-party data collection, and AI innovation.
June 12, 2024

Privacy Management
From legislation to operation: How to prepare for the new wave of US Privacy laws
Prepare your organization for the new wave of US privacy laws.
June 06, 2024

Privacy Management
Understanding data transfers under the GDPR ebook
In the ebook, we delve into the fallout from Schrems II and explore how organizations based in Europe can best navigate international data transfers under the GDPR.
June 05, 2024

Privacy Management
Preparing for a new regulation: Lesson learned from the GDPR businesses can apply to the EU AI act?
Join our panel of experts as we celebrate GDPR Anniversary and take a closer look at the relationship between the GDPR and AI Act.
May 23, 2024

Privacy Management
DSAR Product Demo with Data Privacy Group
Join our webinar to learn the practical tips and use cases for automating DSAR requests.
May 21, 2024

GRC & Security Assurance
Empowering your cyber defense: Key insights into the latest NIST CSF update with PwC
Join this webinar with OneTrust and PwC and gain insights into the upcoming NIST CSF update and learn how to effectively deploy it across your organization.
May 08, 2024

Privacy Management
Best practices for managing employee DSARs in the EU and UK
In this webinar, our panel of experts will explore best practices for managing common complexities experienced when managing DSARs in the EU and UK.
May 08, 2024

Privacy Management
Federal US privacy bill on the horizon? Exploring the draft APRA & new state privacy legislation
Join OneTrust DataGuidance and expert contributors for an overview of the Kentucky Consumer Privacy Act (KCPA), Maryland's Senate Bill 0541, and the draft American Privacy Rights Act and explore how a federal bill could shape the US privacy landscape.
April 23, 2024

Privacy Management
Navigating the data lifecycle with OneTrust Privacy & Data Governance
Explore how OneTrust solutions help you navigate the information lifecycle, ensure compliance, mitigate risks, and enhance data governance practices.
April 22, 2024

Privacy Management
April Privacy & Data Governance Cloud demo webinar
See how OneTrust's Privacy & Data Governance Cloud operationalizes regulatory compliance and helps ensure privacy and responsible data use.
April 17, 2024

Privacy Management
Spring into action! Navigating CPRA: Ensuring compliance and protecting privacy
Join us for an interactive webinar we dive into the CPRA, which will go into force on March 29th.
March 21, 2024

Privacy Management
Navigating data privacy in 2024: Global regulatory updates & compliance strategies
Join our webinar for a comprehensive overview of the latest global data privacy regulations and updates impacting businesses in 2024 and how to prepare.
March 20, 2024

Privacy Management
Preparing to self-certify with the EU-US DPF
The EU-US DPF represents an important mechanism for US-based companies to lawfully transfer personal data form the EU to the US. Use this eBook to learn more about how to self-certify with the framework and its seven core principles.
March 07, 2024

AI Governance
Revisiting IAPP DPI Conference – Key global trends and their impact on the UK
Join OneTrust and PA Consulting as they discuss key global trends and their impact on the UK, reflecting on the topics from IAPP DPI London.
March 06, 2024

Technology Risk & Compliance
PCI DSS Compliance: How to scope and streamline monitoring with Certification Automation
Join our PCI DSS webinar where we discuss how Certification Automation can help free up valuable InfoSec resources, streamline audits, and stay continuously compliant.
March 05, 2024

Privacy Management
Quebec's Law 25: What the CPO wants the CTO to know
Quebec’s Law 25 is a major legislative development in Canadian privacy that will have a significant effect on IT systems. Learn more about what the CPO wants the CTO to know.
February 26, 2024

Catch it Live: See the All-New Features in OneTrust's Winter Release
See the latest OneTrust platform features that improve on customers' ability to build trust, ensure compliance, and manage risk.
February 22, 2024

Privacy Automation
An overview of the Data Privacy Maturity Model
Data privacy is evolving from a regulatory compliance initiative to a customer trust imperative. This data sheet outlines the four stages of the Data Privacy Maturity Model to help you navigate this shift.
February 05, 2024

Privacy Automation
Embedding Privacy by Design through PIA Automation
Join us for a webinar on Embedding Privacy by Design through PIA Automation.
January 11, 2024

Privacy Management
Automating fulfillment of subject rights requests in the US
Learn how Privacy Rights Automation helps to fully automate privacy rights requests.
December 06, 2023

Privacy Management
Live Demo: How to holistically manage data transfers and data sharing requirements
Live demo of the OneTrust Privacy Cloud, exploring how to manage Data Transfers, perform TIAs, and enforce consumer opt-out of the sale/share of personal data.
December 05, 2023

Privacy Management
December's deadline: Ensuring compliance with Utah's privacy regulation
Join us for a webinar as we explore the impending implementation of the Utah Privacy Law, set to take effect on December 31, 2023.
November 14, 2023

Privacy Management
Managing data transfers within the UK & EU
Join our experts as we discuss ways to effectively manage data transfers between the UK & EU while staying compliant with the latest privacy regulations.
October 31, 2023

Privacy Management
Embedding privacy by design to enforce responsible use of data
In this webinar, we explore the latest in Privacy by Design standards and how to effectively manage the balance between Privacy and Data Governance.
October 18, 2023

Privacy Management
Privacy in practice: DSAR with PA Consulting
Join OneTrust and PA Consulting as we deep dive into the latest ICO requirements on SARs, handling DSARs, and the benefits of automation.
September 28, 2023

Privacy Management
Privacy in practice: PIA & DPIA with PA Consulting
Join OneTrust and PA Consulting as we discuss what makes an effective PIA, best practices, and the benefits of automation.
September 21, 2023

Privacy Management
The road to privacy compliance: A spotlight on Oregon & Delaware legislation
We explore the new Oregon and Delaware privacy laws, how they differ from other US privacy laws, and what they mean for your business.
September 14, 2023

Privacy & Data Governance
Privacy in practice for data mapping: With PA Consulting and Syngenta
Join OneTrust and panelists from PA Consulting and Syngenta as we explore practical ways to build an effective data mapping program, best practices, and the need for automation.
September 14, 2023

Governance & Policy Management
EU-US DPF: What next for UK businesses?
Join our expert webinar as we discuss the upcoming UK-US DPF Extension and what UK businesses need to prepare to become DPF-certified.
September 06, 2023

Privacy Automation
The ROI of privacy notice management infographic
Download this infographic and see the ROI benefits of privacy notice management automation with OneTrust Privacy Notice Management.
September 05, 2023

Privacy Management
August Privacy & Data Governance Cloud Demo Webinar
See how OneTrust's Privacy & Data Governance Cloud operationalizes regulatory compliance and helps ensure privacy and responsible data use.
August 16, 2023

Privacy Management
The road to 50 states: Delaware and Oregon join the US privacy landscape
Get in-depth analysis on two upcoming US Privacy laws, the Oregon Consumer Privacy Act (OCPA) and the Delaware Personal Data Privacy Act (DPDPA), with OneTrust DataGuidence and a panel of experts.
August 10, 2023

Technology Risk & Compliance
PCI DSS essentials: A resource collection for compliance
Achieve PCI DSS standard compliance with our comprehsive guide to safeguarding your organization's payment card data.
August 09, 2023

Privacy Management
Managing data transfers
Register for this free webinar to learn how to effectively manage international data transfers in the wake of Schrems II.
July 18, 2023

Responsible AI
Unpacking the EU AI Act and its impact on the UK
Prepare your business for EU AI Act and its impact on the UK with this expert webinar. We explore the Act's key points and requirements, building an AI compliance program, and staying ahead of the rapidly changing AI regulatory landscape.
July 12, 2023

Technology Risk & Compliance
Certification Automation: Managing PCI DSS compliance
See how OneTrust Certification Automation streamlines PCI DSS compliance by identifying controls and requirements with automation.
July 05, 2023

Privacy Management
Unpacking the EU-US DPF
In this webinar, we cover the new EU-US Data Privacy Framework (EU-US DPF) and what privacy program managers need to know for post-Schrems II data transfers.
June 28, 2023

Privacy Management
New states, new dates: Preparing for Indiana, Montana, Tennessee and Florida state privacy laws
Join our expert panel where we examine upcoming privacy legislation in Indiana, Montana, Tennessee, and Florida and the key requirements of each law.
June 20, 2023

Privacy Automation
US privacy laws on the horizon: Which states will be next?
Join our live webinar as OneTrust DataGuidence and privacy experts examine new privacy legislation in Indiana, Montana, Tennessee, Florida, and Texas.
June 15, 2023

Privacy Management
Staying compliant: How to manage data transfers around the globe
In this webinar, we look at the subject of internation data transfers and how to effectively navigate regional laws and mitigate the risk of non-compliance.
June 06, 2023

Privacy Automation
The ROI of DSAR automation
Learn how DSAR automation streamlines privacy rights requests and saves your organization time and resources.
June 01, 2023

Privacy Management
Connecticut Data Privacy Act law book
Get the complete text of the Connecticut Data Privacy Act (CTDPA) for your reference.
May 30, 2023

Privacy Management
Saudi Arabia's PDPL latest amendments: Are you ready?
Join OneTrust and Deloitte Middle East as we cover the latest changes to Saudia Arabia's Personal Data Protection Law (PDPL) and what it means for organizations in the KSA region.
May 30, 2023

Privacy & Data Governance
The 3 priorities of the French DPO: Gain visibility, take action, automate
Download our infographic and learn about the 3 priorities of the French DPO.
May 30, 2023

Privacy Management
GDPR turns 5: Celebrating data protection
Northern Europe panel - Join our panel of experts as they recap the GDPR, its key concepts, and what it means for organizations and compliance.
May 25, 2023

Privacy Management
Global Panel — GDPR & Tech: Key considerations of Privacy by Design and AI in tech
Join our panel of experts as we discuss the impact GDPR had on the tech industry during the past five years, the importance of privacy by design, and what to expect with AI and regulation.
May 25, 2023

Privacy & Data Governance
Global Panel — GDPR & Healthcare: current regulatory guidance and enforcement
In this live webinar, our expert panel examines the first five years of the GDPR, how it changed the healthcare industry, and the changing global regulatory landscape.
May 24, 2023

Privacy Management
Comparing the FADP, Revised FADP, and the GDPR
Download our infographic to see how the Revised FADP compares with its original version and the GDPR.
May 23, 2023

Privacy Management
Global Panel — GDPR & Retail: building customer loyalty and trust with consent and privacy
Join us for a live panel as we discuss GDPR's impact on the retail and eCommerce industry and how companies evolved to meet the global regulatory landscape.
May 23, 2023

Privacy Management
Getting started with GDPR compliance
This eBook covers the fundamental information you need to know in order to get your GDPR compliance program started and how OneTrust helps.
May 23, 2023

Privacy Management
Global Panel — GDPR & Finance: Staying ahead of the regulatory and cyber landscape
How has the GDPR affected the financial industry? Join our live panel as we examine how it companies evolved to meet the regulatory challenges and what can be done to stay ahead of the curve.
May 22, 2023

Privacy & Data Governance
Operationalizing the Iowa Consumer Data Protection Act
Join the Privacy experts at OneTrust for an update on the new law and learn key requirements of Iowa’s new privacy law and more.
May 16, 2023

Privacy Automation
Bridging borders: How to manage international data transfers
This session will cover the regulatory landscape, TIA guidance, and mitigation measures for international data transfers in the wake of the Schrems II case.
April 19, 2023 1 min read

Privacy Automation
OneTrust and Deloitte UK - Data transfers: Assessments & safeguards
OneTrust's Center of Excellence and Deloitte UK will discuss data transfers and GDPR compliance, covering the UK stance, ICO/EDBP guidance, and more.
April 04, 2023 1 min read

Privacy Automation
Privacy by design becomes an ISO standard: What you need to know and how to implement for your business
Get an overview of ISO 31700, learn considerations for implementing a PbD framework for your organization, and a look at our Privacy by Design solutions.
February 16, 2023

Privacy Automation
US Privacy Masterclass - Employee rights fulfilment
Learn the steps you can take to boost employee trust in compliance with US Privacy Laws in our US Privacy Masterclass on Employee Rights Fulfilment.
February 07, 2023

Privacy Automation
US Privacy Masterclass - Consumer rights & opt-outs
Join us in our US Privacy Masterclass as we delve into the evolving US privacy landscape and how you can build a trust-based privacy program in 2023.
February 07, 2023

Privacy Automation
US privacy masterclass - retention & minimization
Our US Privacy Masterclass on Retention & Minimization will help you understand data policy requirements across US Privacy Laws.
February 06, 2023

Privacy Automation
US privacy masterclass - risk and DPIAs
Join us in our US Privacy Masterclass on Risk and DPIAs to understand the operational components for risk assessments/data protection assessments.
February 06, 2023

Privacy Automation
Minimization, retention, and purpose-limitation: evolving privacy to data governance webinar
In this webinar, OneTrust Privacy experts discuss requirements and best practices for governing personal and sensitive data under US state privacy laws.
January 17, 2023 1 min read

Privacy Automation
DSARS: Utilising privacy automation to build a measurable ROI program
We’ll discuss three facets of this problem, such as how to discover, classify and automate your data processes to streamline records of processing activities.
December 07, 2022

Privacy Automation
Minimization, retention, and purpose-limitation: Evolving privacy to data governance
Join this OneTrust webinar to gain insight into how to operationalize and automate retention and minimization requirements.
November 22, 2022

Privacy Automation
Privacy and trust as a strategic imperative webinar
Learn how to go beyond privacy compliance and embrace a data-centric approach to privacy automation and the importance of first-party data collection.
November 18, 2022

Data Discovery & Classification
Mitigating US privacy risk to control your organization’s attack surface
In this session, we'll discuss how the requirements under upcoming US Privacy laws create an opportunity for businesses to embed privacy by default.
November 17, 2022

Privacy Automation
Live demo: Get to know the OneTrust Privacy & Data Governance Cloud
Join a live demo of OneTrust’s Privacy & Data Governance Cloud and discover how to operationalize regulatory compliance and enable trusted data use.
October 25, 2022

Privacy Automation
Putting the impact in PIAs webinar
Watch this webinar to get an overview of how PIAs fit into the Privacy by Design philosophy and gain insight into what an effective PIA looks like.
October 25, 2022

Privacy Automation
Establishing and enforcing retention policies
In this webinar, we will cover data policy requirements across the EU and discuss steps to automate data policy management and operational considerations.
September 05, 2022

Privacy Automation
Don’t just document it, enforce it. Embedding privacy by design into cloud migrations
Learn how businesses can implement governance policies like retention, minimization, and open access through integrating technologies to minimize risks.
September 05, 2022

Privacy Automation
UK panel: Automating the classification and mapping of sensitive data
Join us for this live panel to learn how privacy, security, and data governance professionals can mature their programs beyond tick-the-box compliance activities
May 18, 2022

Privacy Automation
UK panel: How to automate retention policies
Join this live interactive panel to learn how to automatically document, flag violations & enforce retention policies across IT assets.
May 18, 2022

Privacy Automation
OneTrust and Microsoft come together to automate employee rights requests
Join OneTrust and Microsoft in this webinar where we discuss our automated tool for processesing DSAR requests.
May 11, 2022

Privacy Automation
The ultimate guide to privacy program automation
Download our guide and learn how automation allows teams to address broader aspects of their privacy programs such as DSARs, incident management, and more.
April 26, 2022

Privacy & Data Governance
The Ultimate Guide to Privacy Program Automation eBook
Our Ultimate Guide to Privacy Program Automation eBook teaches how automation can help streamline your privacy and governance compliance efforts.
April 26, 2022

Privacy Management
Scaling records of processing with Data Mapping Automation
Discover how automated data mapping increases data accuracy and gives insight into your systems.
April 19, 2022

Privacy Automation
From data compliance to data intelligence
Learn how you can take the first steps towards data intelligence and advance your privacy program to the next phase of automation and maturity.
February 18, 2022

Privacy Automation
4 steps for automating your privacy platform
Automate your privacy program and reduce manual inefficiencies
January 13, 2022

Privacy Automation
Automate your privacy program
Download the checklist and discover the steps you can take to automate critical processes across your privacy program.
December 01, 2021

Privacy Automation
Mastering PIAs & DPIAs: A complete handbook for privacy experts
Unlock the full potential of your privacy program with our complete handbook designed to equip privacy professionals with the essential tools and knowledge for establishing robust PIA and DPIA processes.
July 22, 2021

Consent & Preferences
OneTrust Consent & Preference Management demo
Watch this demo video to learn how OneTrust Consent and Preference Management Cloud streamlines the consent lifecycle and accelerates fulfillment.
October 24, 2020

Privacy Management
Navigating Canadian consumer rights requests
Join our webinar to learn how to effectively manage DSARs and comply with Quebec's Law 25, ensuring your organization meets customer and regulatory expectations.

Privacy Automation
Privacy Automation demo
Automate DSR fulfillment, track regulations, maintain an evergreen data map, and so much more — all in one powerful privacy solution.

Privacy Management
Privacy in Practice with PA Consulting
Join OneTrust and expert speakers from PA Consulting for a webinar series discussing the need-to-knows for creating a successful privacy management program in your organization.

Privacy Automation
PIA and DPIA demo webinar with Data Privacy Group
Join our webinar to learn the benefits of automating your PIAs and DPIAs using the OneTrust platform

